DataStax
This guide will walk you through integrating Common Fate with DataStax. By the end of this guide, you’ll have a functioning integration with Common Fate, allowing it to provision access to DataStax Roles.
DataStax Setup
To configure the DataStax integration, follow these steps to create an Application Token in your DataStax console. First, Sign In into DataStax.
A. Create the Role for the API Token:
- Browse to Settings > Role
- Click Add Custom Role
- Enter a name e.g ‘Common Fate Provision Role’
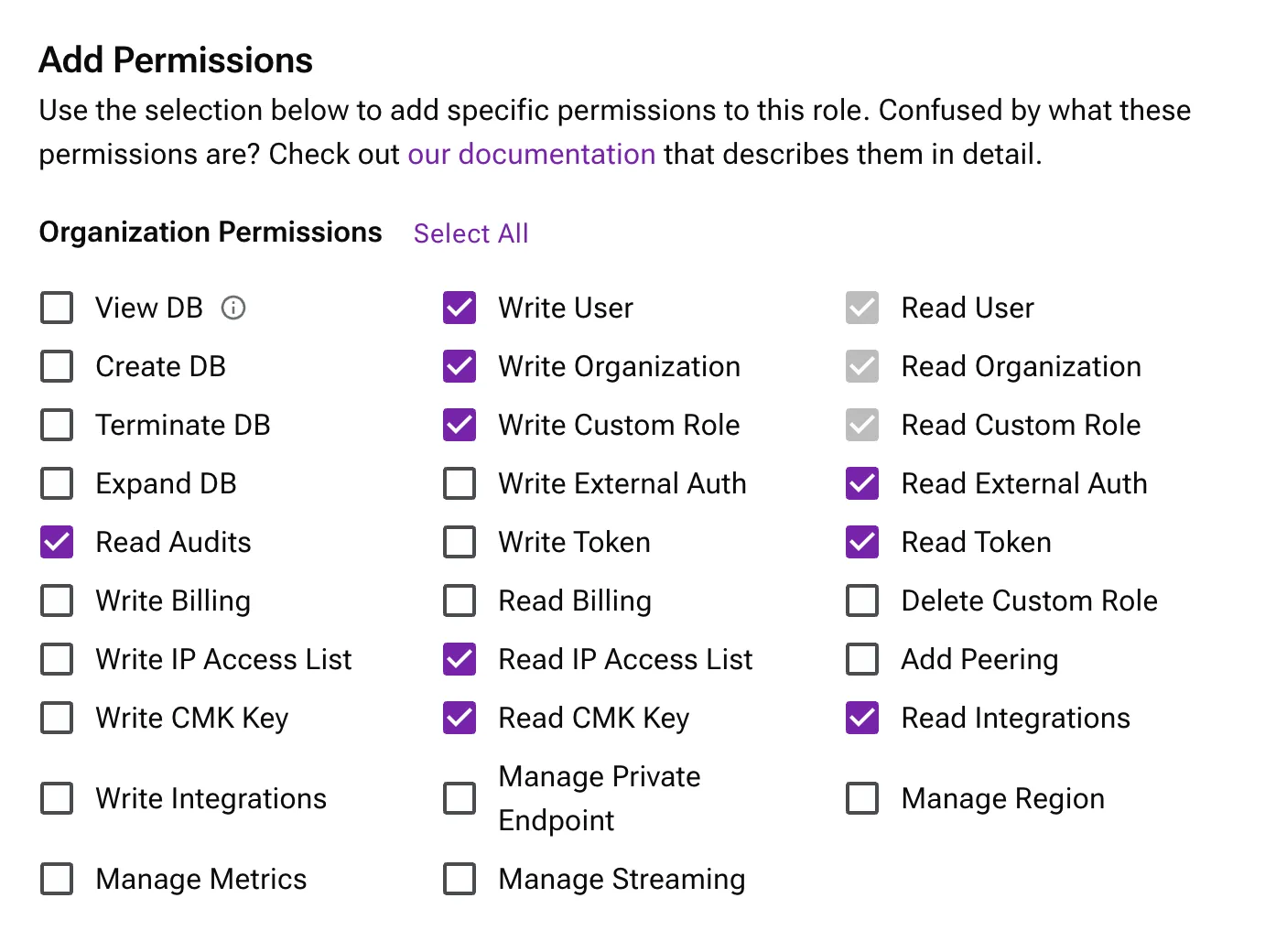
- Select the following permissions:
- Read Audits
- Write User
- Write Organization
- Write Custom Role
- Read IP Access List
- Read CMK Key
- Read External Auth
- Read Token
- Read Integrations
- Click Create Role
B. Create the API Token:
- Browse to Settings > Tokens.
- Select the Role you created
- Click Generate Token
- Save the newly created token somewhere safe for the next steps.
You will need to create a new SecretString in SSM Parameter Store and then use the path when configuring your deployment in Terraform.
You can use the AWS CLI to create a secret in the region you are deploying to. you must use the following path "/<namespace>/<stage>/<secret name>".
aws ssm put-parameter \ --name "/common-fate/prod/datastax-api-key" \ --value "mySecretValue" \ --type "SecureString"Configuring Common Fate
In this section, you will register the DataStax integration with your Common Fate deployment. At the end of this section you should have Common Fate ready to provision access. You’ll need to have set up the Common Fate Application Configuration repository using our Terraform provider.
Inside your Application Configuration repository, add the following module:
resource "commonfate_datastax_integration" "DataStax" { name = "DataStax" api_key_secret_path = "/common-fate/prod/datastax-api-key"}Apply the changes. If the apply succeeds, you should see the integration appear on the settings page in the web dashboard.
Provisioning access to DataStax Roles
You can now create an access workflow and availabilities:
locals { datastax_org_id = <Your DataStax Org ID>}
resource "commonfate_access_workflow" "datastax" { name = "DataStax" access_duration_seconds = 60 * 60 * 2 priority = 1}
resource "commonfate_selector" "datastax_org" { id = "datastax_org" resource_type = "DataStax::Organization" belonging_to = { type = "DataStax::Organization" id = local.datastax_org_id } when = <<EOT true EOT}
resource "commonfate_availability_spec" "datastax" { workflow_id = commonfate_access_workflow.demo.id role = { type = "DataStax::Role" id = <Your DataStax Role ID> }
target = { type = "Access::Selector" id = commonfate_selector.datastax_org.id } identity_domain = { type = "DataStax::Organization" id = local.datastax_org_id }}